Why HTTPS
You might have heard that using public wifi is insecure but how insecure can it really be? Whenever you are connected to any network the data that you exchange with any other computer has to be sent over that network and it does not follow a straight path, it can pass through many servers to reach the destination. Remember a server is just someone else’s computer. That seems a little scary to say the least, especially as most communication protocols use text. Lets see how hard it is to looks at this kind of information.
Basic HTTP / TCP connection
Lets say you visit a website for your bank, in your web browser you enter http://www.bank.com. The request for that domain is resolved by your domain server, then a tcp connection is opened to the bank’s server. There are quite a few steps to establish the connection, but it’s not the focus here. When the connection is established the web browser will send a packet containing the HTTP request that look like the following.
GET / HTTP/1.1
User-Agent: Mozilla/4.0 (compatible; MSIE5.01; Windows NT)
Host: www.bank.com
Accept-Language: en-us
Accept-Encoding: gzip, deflate
Connection: Keep-Alive
This packet will now be broadcast across the networks and each server between source and destination will pass it on if it is not intended for that server. = The target server will receive this message and will parse the message and will recognise the route of “/” as the home page also known as the index.html, or equivalent for responsive websites. The server will then build a http packet of it’s own and send it back to the client, where the web browser will parse the response and render the web page on screen. HTTP is a text protocol which means the packet will contain clear text, lets see what this look like in real life.
Sniffing TCP Packets
For my test I will start a basic HTTP server using python’s SimpleHTTPServer. I create a small page with a username and password box and a submit button.
# Create a test working directory
mkdir ./simpleServer
cd ./simpleServer
# Create an example bank login page,
echo '<h1>Welcome to Bank.com</h1>
<form action="/login.html" method="post">
username: <input type="test" name="username">
<br/>
password: <input type="password" name="password">
<br/>
<input type="submit" name="login">
</form>' > index.html
echo '<h1>Logged In \o/</h1>
<h2> Hello User</h2>' > login.html
python -m SimpleHTTPServer 8080
Yes this is a very simple example but it does transfer to any other website available on the internet including your bank, the government or facebook.
Next we will setup tcpdump and to listen on the network the server is running on. tcpdump is an open source TCP packet monitoring tool that is used for network sniffing and traffic analysis. I’m running on a UNIX based system and it is usually installed by default. Alternatively you could use Wireshark you can get the same result.
sudo tcpdump -i lo0 -v -XX
# i specifies the interface, lo0 is the local loopback
# v turns on Verbose output
# XX outputs packet data as ASCII and Hex
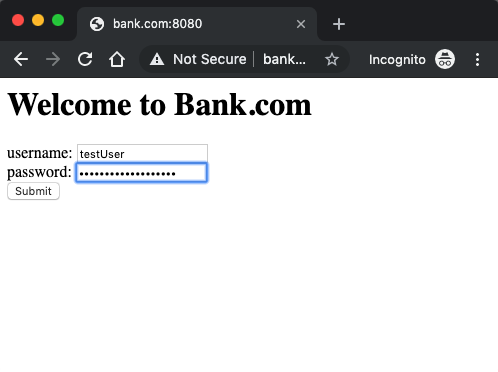
We will enter a username and password and press submit:
❯ sudo tcpdump -i lo0 -XX tcp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on lo0, link-type NULL (BSD loopback), capture size 262144 bytes
17:13:58.926521 IP localhost.51768 > localhost.http-alt: Flags [P.], seq 1:687, ack 1, win 6379, options [nop,nop,TS val 1037584317 ecr 1037584317], length 686: HTTP: POST /login.html HTTP/1.1
0x0000: 0200 0000 4500 02e2 0000 4000 4006 0000 ....E.....@.@...
0x0010: 7f00 0001 7f00 0001 ca38 1f90 4080 e782 .........8..@...
0x0020: f229 9640 8018 18eb 00d7 0000 0101 080a .).@............
0x0030: 3dd8 47bd 3dd8 47bd 504f 5354 202f 6c6f =.G.=.G.POST./lo
0x0040: 6769 6e2e 6874 6d6c 2048 5454 502f 312e gin.html.HTTP/1.
0x0050: 310d 0a48 6f73 743a 2062 616e 6b2e 636f 1..Host:.bank.co
0x0060: 6d3a 3830 3830 0d0a 436f 6e6e 6563 7469 m:8080..Connecti
0x0070: 6f6e 3a20 6b65 6570 2d61 6c69 7665 0d0a on:.keep-alive..
0x0080: 436f 6e74 656e 742d 4c65 6e67 7468 3a20 Content-Length:.
0x0090: 3539 0d0a 4361 6368 652d 436f 6e74 726f 59..Cache-Contro
0x00a0: 6c3a 206d 6178 2d61 6765 3d30 0d0a 4f72 l:.max-age=0..Or
0x00b0: 6967 696e 3a20 6874 7470 3a2f 2f62 616e igin:.http://ban
0x00c0: 6b2e 636f 6d3a 3830 3830 0d0a 5570 6772 k.com:8080..Upgr
0x00d0: 6164 652d 496e 7365 6375 7265 2d52 6571 ade-Insecure-Req
0x00e0: 7565 7374 733a 2031 0d0a 444e 543a 2031 uests:.1..DNT:.1
0x00f0: 0d0a 436f 6e74 656e 742d 5479 7065 3a20 ..Content-Type:.
0x0100: 6170 706c 6963 6174 696f 6e2f 782d 7777 application/x-ww
0x0110: 772d 666f 726d 2d75 726c 656e 636f 6465 w-form-urlencode
0x0120: 640d 0a55 7365 722d 4167 656e 743a 204d d..User-Agent:.M
0x0130: 6f7a 696c 6c61 2f35 2e30 2028 4d61 6369 ozilla/5.0.(Maci
0x0140: 6e74 6f73 683b 2049 6e74 656c 204d 6163 ntosh;.Intel.Mac
0x0150: 204f 5320 5820 3130 5f31 345f 3229 2041 .OS.X.10_14_2).A
0x0160: 7070 6c65 5765 624b 6974 2f35 3337 2e33 ppleWebKit/537.3
0x0170: 3620 284b 4854 4d4c 2c20 6c69 6b65 2047 6.(KHTML,.like.G
0x0180: 6563 6b6f 2920 4368 726f 6d65 2f37 342e ecko).Chrome/74.
0x0190: 302e 3337 3239 2e31 3639 2053 6166 6172 0.3729.169.Safar
0x01a0: 692f 3533 372e 3336 0d0a 4163 6365 7074 i/537.36..Accept
0x01b0: 3a20 7465 7874 2f68 746d 6c2c 6170 706c :.text/html,appl
0x01c0: 6963 6174 696f 6e2f 7868 746d 6c2b 786d ication/xhtml+xm
0x01d0: 6c2c 6170 706c 6963 6174 696f 6e2f 786d l,application/xm
0x01e0: 6c3b 713d 302e 392c 696d 6167 652f 7765 l;q=0.9,image/we
0x01f0: 6270 2c69 6d61 6765 2f61 706e 672c 2a2f bp,image/apng,*/
0x0200: 2a3b 713d 302e 382c 6170 706c 6963 6174 *;q=0.8,applicat
0x0210: 696f 6e2f 7369 676e 6564 2d65 7863 6861 ion/signed-excha
0x0220: 6e67 653b 763d 6233 0d0a 5265 6665 7265 nge;v=b3..Refere
0x0230: 723a 2068 7474 703a 2f2f 6261 6e6b 2e63 r:.http://bank.c
0x0240: 6f6d 3a38 3038 302f 0d0a 4163 6365 7074 om:8080/..Accept
0x0250: 2d45 6e63 6f64 696e 673a 2067 7a69 702c -Encoding:.gzip,
0x0260: 2064 6566 6c61 7465 0d0a 4163 6365 7074 .deflate..Accept
0x0270: 2d4c 616e 6775 6167 653a 2065 6e2d 4742 -Language:.en-GB
0x0280: 2c65 6e3b 713d 302e 392c 656e 2d55 533b ,en;q=0.9,en-US;
0x0290: 713d 302e 382c 6672 3b71 3d30 2e37 2c64 q=0.8,fr;q=0.7,d
0x02a0: 653b 713d 302e 360d 0a0d 0a75 7365 726e e;q=0.6....usern
0x02b0: 616d 653d 5465 7374 5573 6572 2670 6173 ame=TestUser&pas
0x02c0: 7377 6f72 643d 5375 7065 7253 6563 7265 sword=SuperSecre
0x02d0: 7450 6173 7377 6f72 6426 6c6f 6769 6e3d tPassword&login=
0x02e0: 5375 626d 6974 Submit
The part we are interested in is the data from address 0x02a0.
username=TestUser&password=SuperSecretPassword&login=Submit
You will see that the data from the POST is clear text and the password here is ‘SuperSecretPassword’, this data will be sent over a computer network exactly like this, and that is why HTTPS is important.
HTTPS Communication / Secure TCP
Next we will repeat the same steps as above with the exception that the server now runs with TLS, which means the address of the web page is now https://bank.com:8080. The resulting packets that we capture from tcpdump is listed below:
❯ sudo tcpdump -i lo0 -XX tcp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on lo0, link-type NULL (BSD loopback), capture size 262144 bytes
19:32:42.935715 IP localhost.52623 > localhost.http-alt: Flags [P.], seq 1:519, ack 1, win 6379, options [nop,nop,TS val 1045848762 ecr 1045848762], length 518: HTTP
0x0000: 0200 0000 4500 023a 0000 4000 4006 0000 ....E..:..@.@...
0x0010: 7f00 0001 7f00 0001 cd8f 1f90 449a 33d5 ............D.3.
0x0020: 1536 90b6 8018 18eb 002f 0000 0101 080a .6......./......
0x0030: 3e56 62ba 3e56 62ba 1603 0102 0101 0001 >Vb.>Vb.........
0x0040: fd03 0346 d43f 7cd5 d42b ecfa a6cc e1f2 ...F.?|..+......
0x0050: ec0a c40d b6f8 8487 3361 816d 52fb fd8a ........3a.mR...
0x0060: c5b9 5d20 9a4a 24cf f685 a2b8 756f b49a ..]..J$.....uo..
0x0070: cb29 fc91 2b6c c82a 621c bb3d 5e52 f7a3 .)..+l.*b..=^R..
0x0080: 7e68 6237 0022 8a8a 1301 1302 1303 c02b ~hb7.".........+
0x0090: c02f c02c c030 cca9 cca8 c013 c014 009c ./.,.0..........
0x00a0: 009d 002f 0035 000a 0100 0192 2a2a 0000 .../.5......**..
0x00b0: 0000 000d 000b 0000 0862 616e 6b2e 636f .........bank.co
0x00c0: 6d00 1700 00ff 0100 0100 000a 000a 0008 m...............
0x00d0: 2a2a 001d 0017 0018 000b 0002 0100 0023 **.............#
0x00e0: 00d0 5c4a 218a 5ac0 7886 8816 3bf8 2e4b ..\J!.Z.x...;..K
0x00f0: 9b00 07bc 33a1 e041 5da9 ef66 c397 c5d0 ....3..A]..f....
0x0100: c634 ab9a 4647 ec51 9995 00a5 4d2b 6a29 .4..FG.Q....M+j)
0x0110: 1a7a d231 a8ba c127 1bff 275b 71d5 cbce .z.1...'..'[q...
0x0120: ecba 71d7 3b0f d687 e8e1 7a27 7d9b 4075 ..q.;.....z'}.@u
0x0130: 9a76 7c57 909a 3fa1 7bc4 65a8 90c9 4b1f .v|W..?.{.e...K.
0x0140: 1850 ad6d 6f73 6780 b342 5e8f ae81 99ea .P.mosg..B^.....
0x0150: 1950 3275 8d56 b015 09a5 42b2 75d5 cef1 .P2u.V....B.u...
0x0160: 8b99 1742 1f69 0e70 835b 7ae9 dc1d 56a7 ...B.i.p.[z...V.
0x0170: f6a0 b300 a47c 0282 e421 0cbf f506 3583 .....|...!....5.
0x0180: bdce 493d e2b0 3b3f 137e e607 e866 7cef ..I=..;?.~...f|.
0x0190: 88a4 0e03 9c66 4803 f7b5 049d 3c1b 55f8 .....fH.....<.U.
0x01a0: 30de d319 19e8 b478 74bf 1587 d554 12ba 0......xt....T..
0x01b0: ff47 0010 000e 000c 0268 3208 6874 7470 .G.......h2.http
0x01c0: 2f31 2e31 0005 0005 0100 0000 0000 0d00 /1.1............
0x01d0: 1400 1204 0308 0404 0105 0308 0505 0108 ................
0x01e0: 0606 0102 0100 1200 0000 3300 2b00 292a ..........3.+.)*
0x01f0: 2a00 0100 001d 0020 27d4 4c62 6e84 b64a *.......'.Lbn..J
0x0200: 9866 f761 bcaa 9b56 3483 db0e 5029 533f .f.a...V4...P)S?
0x0210: dd36 a40d b159 1e60 002d 0002 0101 002b .6...Y.`.-.....+
0x0220: 000b 0aba ba03 0403 0303 0203 0100 1b00 ................
0x0230: 0302 0002 4a4a 0001 0000 1500 0100 ....JJ........
Looking at the data part of the of the packets we can see tha the data is now encrypted. The Public Key Cryptographic algorithm uses public-private key pars to perform authentication and encryption. Only the server with the private key can decrypt the data that was encrypted using the server’s public key. Unless the attacker is able to get hold of the private of the server they cannot decrypt the packet, making your communication more secure.
Conclusion
HTTPS is crucial when doing anything on the internet. I recommend using a browser plugin that force HTTPS like HTTPS Everywhere, every time you browse to a website it transforms the address to request a HTTPS version of that website.