CLI Tools & Last Pass CLI
Managing API Keys and Secrets when working with CLI’s can be and interesting security challenge. Keeping CLI tools logged in exposes cloud systems to exploitation of tools like AWS cli, Azure CLI or MongoDB CLI on development machines.
Ensuring tools log out when systems lock or restart can ensure online systems stay safe, but the repeated logins every time you try and update your infrastructure make this process tedious and repetitive.
One option is to store your secrets in a password manager like LastPass or 1password, the combination of a secure encryption systems, a GOOD password and multi factor authentication will keep your keys locked away safely.
LastPass offers lpass, a command line tool to interact with your LastPass vault and 1password offers op with similar functionality.
Lets see how we can achieve a secure tools set with as little work as possible.
Ignore Important calls
We want to ensure we ignore all lpass commands in the history, that way no one can see any commands in the system history. We add lpass and our bash functions to the ignore list.
We add the HISTORY_IGNORE environment variable and set the histignorespace option. Combined with the aliases for lpass we ensure even if we type a new command we never leave any trace in the history.
#Options
HISTORY_IGNORE="(lpass|lpass|aws_login|real_login|mongo_cli_login)"
setopt histignorespace
#Aliases
alias lpass=" lpass"
alias lpassc=" lpass show -q --password -c"
Create your Server Entry
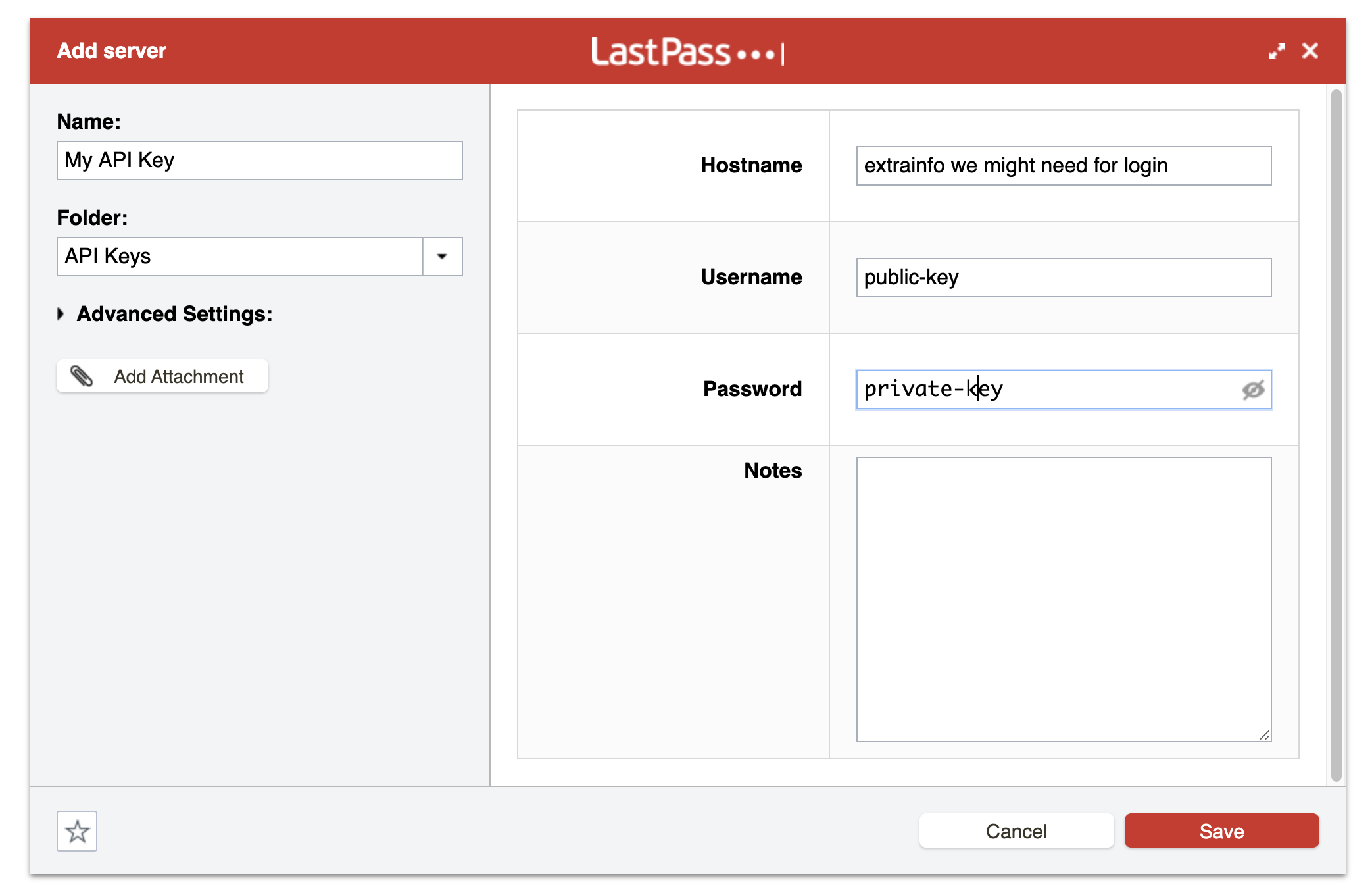
Add a new server entry to LastPass, setting the username as the public key, and the private key as the password. Set the Name as the unique identifier we want to use to log into the cli tool. I always group all my API Keys together in a folder called API Keys. Additional options like projectId or org name can be stored in the hostname for later use.
Login Functions
Login function for AWS CLI.
fucntion aws_login() {
ENTRY_ID=$(lpass ls "API Keys" | grep "$1" | tail -c 21 | head -c 19)
aws configure set aws_access_key_id $(lpass show $ENTRY_ID --username)
aws configure set aws_secret_access_key $(lpass show $ENTRY_ID --password)
}
Login function for realm-cli.
function realm_login () {
ACCOUNT_ID=$(lpass ls | grep "$1" | tail -c 21 | head -c 19)
realm-cli login --api-key $(lpass show $ACCOUNT_ID --username) --private-api-key $(lpass show $ACCOUNT_ID --password)
}
Login function for mongocli
function mongo_cli_login () {
ACCOUNT_ID=$(lpass ls "API Keys" | grep "$1" | tail -c 21 | head -c 19)
mongocli config set public_api_key $(lpass show $ACCOUNT_ID --username)
mongocli config set private_api_key $(lpass show $ACCOUNT_ID --password)
mongocli config set project_id $(lpass show $ACCOUNT_ID --field=Hostname)
}
Automatic logouts and cleanups
Now we need to ensure we cleanup as many of the cli tools on logout.
Create a new file and make it executable, ensure you lock this down as much as possible.
touch /bin/logout-tools
sudo chmod +x /bin/logout-tools
sudo chmod 400 /bin/logout-tools
We add the logout script to the relevant logout hook on Mac:
sudo defaults write com.apple.loginwindow LogoutHook /bin/logout-tools
Next we add the various commands to the script to ensure there are clean logouts
lpass logout --force
realm-cli logout
az logout
mongocli config delete default --force
rm -rf ~/.aws/credentials
Conclusion
Working with CLI tools can be a very effective way of interacting with various cloud based services, but keeping them safe can be a tedious task.
Making use of a variety of readily available tools we can secure these tools in a few simple steps.